A well-designed phishing email was aimed at cPanel users recently, being able to tell a Phishing email is very important for your online security.
What is a Phishing email?
Phishing, by definition, is the act of attempting to acquire a person’s information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity. Phishing emails can be sent to any email address and most phishing attempts are done through email. The most tricky phishing emails make use of e-mail spoofing, where the ‘from’ address that your mail clients display seems to be valid. These emails will include a link that directs users to enter details at a fake website. This fake website will have the same look-and-feel as the legitimate one and are often nearly identical to the real one. In some cases they will register a domain to look like the website they are trying to get your details for. Something close for example to fake Web Host Pro they might get webhoost.pro and hope you don’t notice the extra letter.
How Phishing Emails Affects You
Popular website users are some of the easiest targets out there. At Web Host Pro we take steps to help end users more easily weed out some of the obvious offenders by using strict SPF records, but that doesn’t prevent all attacks. Understanding, reporting, and mitigation is key to preventing the effectiveness of these attacks.
What to do if you get a Phishing Email
The first step if you think you’ve received a phishing email is to confirm it.
- Check the full email headers for the ‘Sender’ address
- Check for links, logos, typos included in the email
- Typos, misspellings, and incorrect capitalization are red flags
- URLs or names that aren’t quite right (e.g., webhoost.pro webhot.pro) are red flags
Report the URL to https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
Reporting will block the URL in Chrome, Firefox, Android, iPhone, Google, and more
Report the URL to https://www.microsoft.com/en-us/wdsi/support/report-unsafe-site
Reporting will block the URL in Edge, Office 365, and Internet Explorer
Forward the email, including the full headers, to reportphishing@apwg.org
What do they look like?
An example of the recent cPanel phishing email is below.
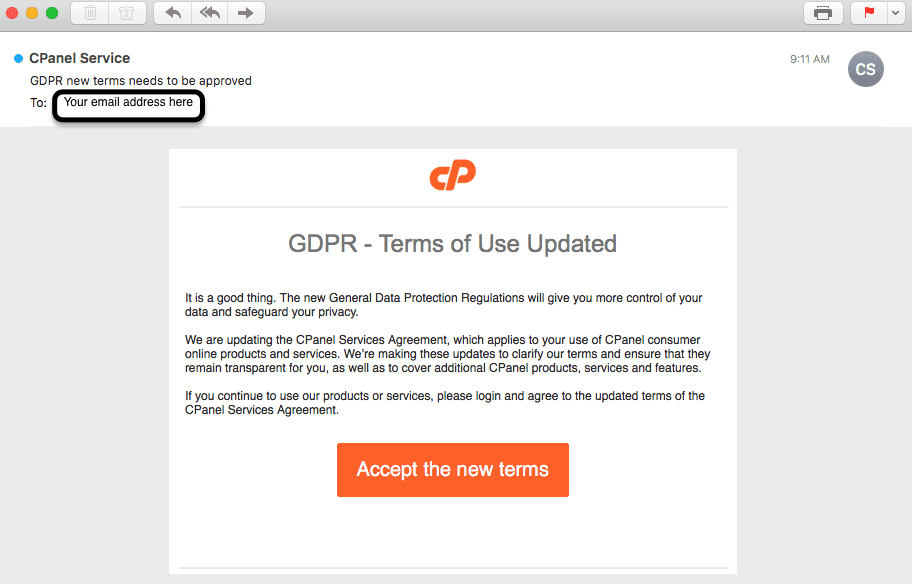
Notice that the content has very few typos, but the ‘from’ address has an incorrectly capitalized ‘CPanel.’ If you were to click on the ‘Accept the new terms’ button, you would be taken to a legitimate-looking form that appeared to be a cPanel login page, but the URL didn’t have cPanel anywhere it in.
I got tricked and put your credentials in there!
If you fell for the trick (as so many people have), the first step is to change the password for the account ASAP. If you have used that password anywhere else, change the password there, too. It’s best to make a plan to sign up for a password manager and start making unique passwords for each account you have. We like DashLane which also happens to be free!
To sum up..
Phishing attacks often display spoofed email addresses, to trick receivers into believing they are coming from legitimate users in hopes to send users to a site that has a legitimate design, and ask for a user’s legitimate login, password, and/or other personal details. If you happen to fall for one, make sure and change your password right away. Long term use a password manager that makes separate logins for each site.

